Automatic AI Analysis for Electrical Schematics
Spend your time on the core design
let CADY oversee the technical details

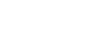











CADY’s AI ingests and understands component datasheets offline
CADY’s AI automatically retrieves information from millions of datasheets of electrical components and understands their properties and requirements.
It then builds a formal language database for all components in the market, which updates whenever a new datasheet revision appears.
Deep Schematic Analysis
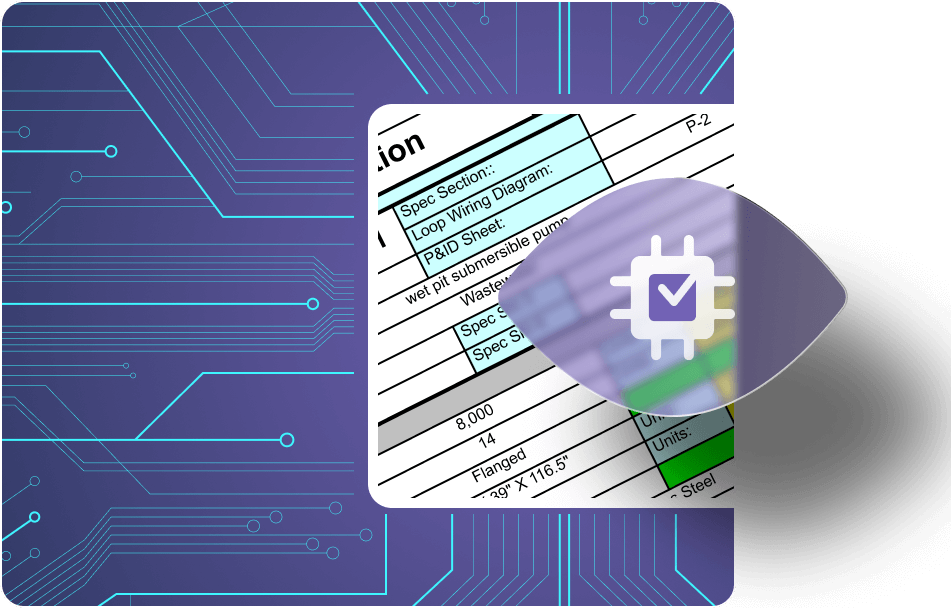
CADY utilizes the component datasheets information to analyze the schematic from different angles –
Connection integrity, voltage mapping, communication validity, best-practice rules, and more
Concise Findings Report
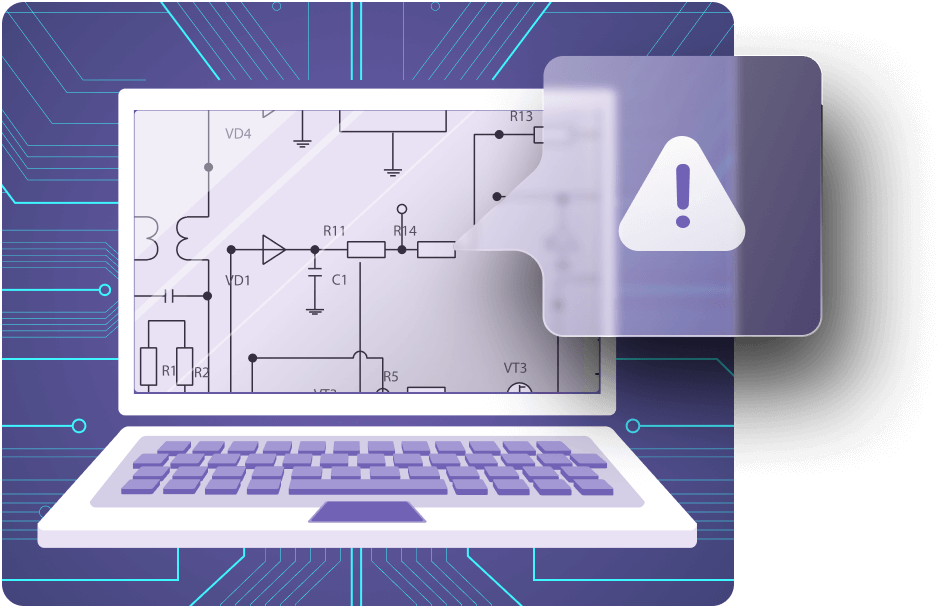
“CADY generates an interactive report, grouping errors, warnings, and best practice recommendations from different categories, allowing the user to review the report within minutes.
Each finding can be marked and commented to track the progress of the board design from one revision to the next

CADY’s AI ingests and understands component datasheets offline
CADY’s AI automatically retrieves information from millions of datasheets of electrical components and understands their properties and requirements.
It then builds a formal language database for all components in the market, which updates whenever a new datasheet revision appears.

Deep Schematic Analysis
CADY utilizes the component datasheets information to analyze the schematic from different angles –
Connection integrity, voltage mapping, communication validity, best-practice rules, and more

Concise Findings Report
“CADY generates an interactive report, grouping errors, warnings, and best practice recommendations from different categories, allowing the user to review the report within minutes.
Each finding can be marked and commented to track the progress of the board design from one revision to the next
How it works
AI-Powered Analysis
Built for Modern Circuit Design

AI that knows how components really work, not just what they’re called

Drag and Drop your Netlist and BOM to run a fully automated, deep schematic checks with zero setup.

Deep analysis, covering a wide-range of errors over the whole circuit – from a basic resistor to the most complex FPGA.

We never store your netlists or BOM files. Your data stays private, safe, and compliant
Data
security
At our core, we recognize the critical importance of confidentiality and data protection, particularly in handling sensitive information relating to electrical schematics.
Our platform is built with dedication to security, adhering to industry standards and tailored to safeguard data based on its sensitivity and confidentiality requirements.
CADY does not permanently store these files, prioritizing the security and privacy of your data.
All data is encrypted using best in class encryptions, at both transit and rest.
Incoming traffic to CADY undergoes filtration through multiple layers of protection, including a Web Application Firewall (WAF), reinforcing the platform’s security.
CADY takes advantage of various security functions, services, and tools provided by Cloud vendors.
Regular assessments and penetration tests are conducted for CADY to identify potential vulnerabilities. Executive summary reports are available to customers upon request, subject to a non-disclosure agreement (NDA).

Data
security
At our core, we recognize the critical importance of confidentiality and data protection, particularly in handling sensitive information relating to electrical schematics.
Our platform is built with dedication to security, adhering to industry standards and tailored to safeguard data based on its sensitivity and confidentiality requirements.
CADY does not permanently store these files, prioritizing the security and privacy of your data.
All data is encrypted using best in class encryptions, at both transit and rest.
Incoming traffic to CADY undergoes filtration through multiple layers of protection, including a Web Application Firewall (WAF), reinforcing the platform’s security.
CADY takes advantage of various security functions, services, and tools provided by Cloud vendors.
Regular assessments and penetration tests are conducted for CADY to identify potential vulnerabilities. Executive summary reports are available to customers upon request, subject to a non-disclosure agreement (NDA).
