The Malicious Supabase Agent Attack
The Price of Agentic Freedom: When LLMs Get Tricked Model Context Protocol (MCP) has emerged as the standard way for agents to interact with external...4 min read
Differential Privacy VS Data Masking: The Evolution of Privacy-preserving Methods
With the advent of artificial intelligence, companies are increasingly turning to advanced privacy-preserving methods to safeguard their data. Two prominent techniques in this arena...9 min read
Building a Successful Data Platform Strategy Today
The ability to collect, process, and derive insights from vast amounts of information is a necessity for businesses looking to stay competitive today (see...9 min read
Essential Features of an Enterprise Data Platform for Optimized Performance
As data volumes continue to grow exponentially, organizations are increasingly relying on enterprise data platforms (EDP) to manage, analyze, and derive value from their...11 min read
Data Access Management in the AI Era
As AI technologies, particularly generative AI, continue to advance and find more applications across various industries, the demand for high-quality, diverse datasets is likely...10 min read
The European Data Act: A New Era for Privacy Regulation
The rapid advancement of technology, with the proliferation of smart devices, social media platforms, and cloud-based services, has brought about a myriad of challenges...10 min read
Why Your Financial Data Infrastructure is Critical
The term “financial data” covers everything from daily transactions to complex data like market movements, economic indicators, and company performance. Organizations actively collect and...5 min read
A Comprehensive Explanation of The Executive Order on the Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence
AI, or artificial intelligence, has changed how we interact with technology. This shift has come in all shapes and sizes since the early releases...6 min read
Effective Strategies for Access Control and Permission Management in Sensitive Environments
Consider this scenario: A financial institution has not implemented access control. Employees at all levels, including interns and administrative staff, have unrestricted access to clients’...6 min read
What is Data Access Governance, and Why Is it so Important?
Organizations are amassing vast amounts of information, including sensitive and confidential data. Effective data management has become a critical concern, not only for regulatory...9 min read

Your Database, Virtualized for AI.
Connect your internal data sources to GenAI. Live, scoped, secure.
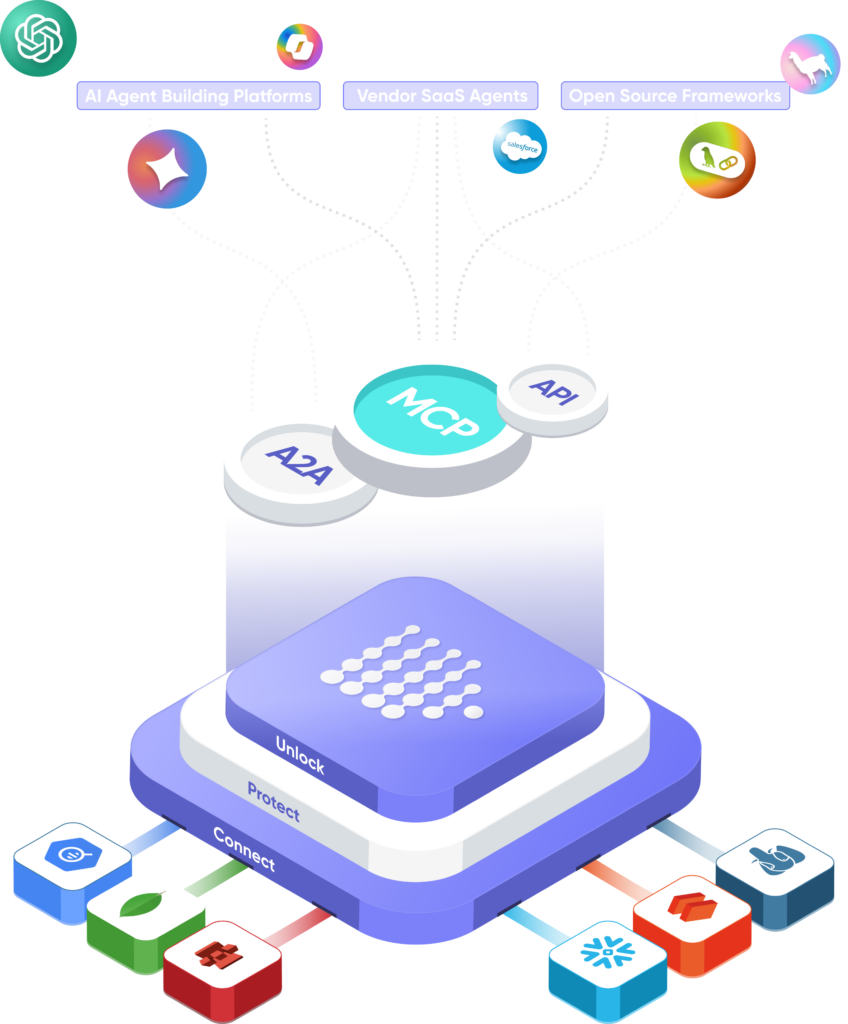
Virtually Your Database, AI-Ready.
Connecting AI agents to personal standalone applications is easy. Connecting them to core business data, where the real value lies, is still painfully hard.
PVML makes it possible:
- Connect: All data, live, no duplication
- Protect: Proprietary mathematical protection
- Unlock: AI-agnostic, get an instant MCP/A2A/API
Connect:
Data Stack Agnostic
PVML’s unified data access layer connects to any data source – without duplication or data movement. Our high-performance Golang connectors deliver low-latency & frictionless access across systems.
Protect:
Differential Privacy & Security Engine
Our runtime privacy engine dynamically scopes data for every agent and user — enforcing policy-based access controls with differential privacy, filtering, masking, and live validations.
Unlock:
Plug Into Any AI
PVML auto-generates secure, context-aware access protocols (MCPs, A2As, APIs), enabling any agent, model, framework, or vendor to connect without infrastructure changes.
Monitor:
Auditability & Governance
Every agent action – from query to response – is logged. PVML delivers full audit trails for enterprise-grade compliance.
Security and Compliance
PVML provides a secure foundation that allows you to push the boundaries. We undergo strict external audits to ensure our solution adheres to the highest standards of privacy and security.

Future Proof Your AI Innovation with PVML
Privacy
Protection &
Compliance
Maintain complete control over permissions, access, and auditability while ensuring compliance with the highest data privacy standards of the AI era.
Faster Rollouts
Reduce engineering costs and accelerate time-to-production by instantly plugging scoped, virtual databases to GenAI without unnecessary data duplication or hardcoded, manual configurations.
Flexibility to Innovate
Stay ahead of the curve and avoid vendor lock-in by seamlessly adopting new AI models, protocols, and data sources.
Visibility & Control
Manage all data access, permissions, and privacy policies from a single, centralized system for complete governance, audit and security.
Optimized AI
Provide AI with the perfect scope of data, including its dynamic, semantic context.
Broader Data Access
Unlock previously restricted data, safely expand AI access across teams, and enable secure third-party collaboration.
Use Cases

Analyze Data with AI
Unlocking access with AI requires strong privacy
capabilities, ability to analyze live data and guarantees
that results are trustworthy and based on the data.
With PVML, you can enforce permissions on live chats,
empower your users to analyze data in real time using
free text and see how results were generated for explainability.
Read about our case study featuring a fintech company
that sped up time to insight by giving employees access
to a live chat with their data.

Anonymization
Sharing data between business units poses challenges
due to different data-owners, multiple data sources, and
various security concerns.
With the integration of PVML’s data access platform, all
data sources can be centralized, promoting collaboration
across business units without compromising privacy.
Read about our case study featuring an insurance company
that enhanced the quality and speed of business insights by
unlocking internal collaboration.

Monetization
Monetizing data requires strong privacy guarantees to
ensure trust and compliance, but also convenient ways
for the 3rd parties to extract value from this data.
Our platform allows companies to monetize insights
derived from data without risking customers’ privacy,
alongside both AI-based options to analyze the data.
Read about our case study with a telecom company
seeking for privacy-preserving ways of sharing insights
from data with non-technical 3rd parties.
Latest blog posts
Explore Our Recent Insights and Updates.
Frequently Asked Questions
Everything you need to know.



